Among the growing success and adoption of decentralized social networks, there is one that stands out above the rest for its exceptional explosion. Farcaster.
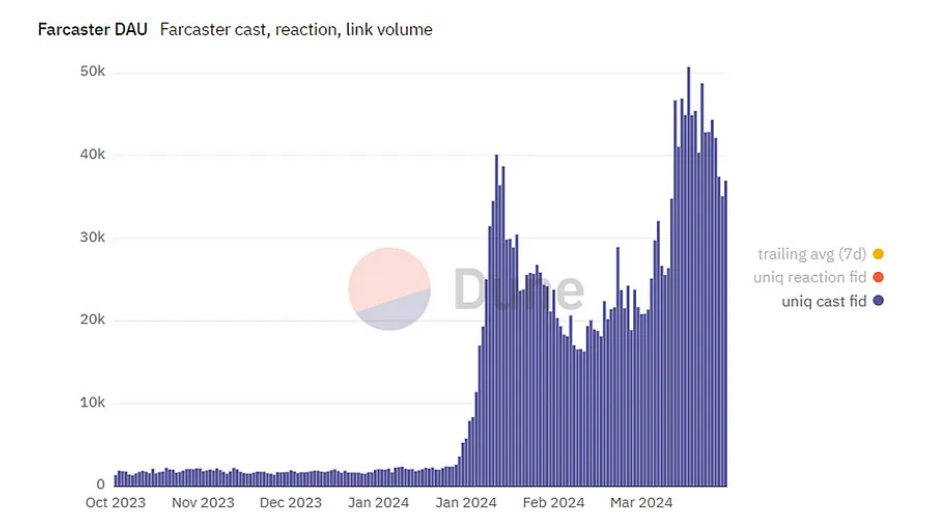
As we can see, since the beginning of 2024 the number of users in this social network has increased considerably.
Let’s see what Farcaster is and how it works.
A sufficiently decentralized social network
This is Farcaster’s slogan and what they have built.
For them, a sufficiently decentralized social network is one in which users interact with each other without anyone being able to stop them.
While in decentralized social networks companies can censor people and limit the scope of their publications, Farcaster proposes a model in which each user owns their account and their publications.
The key to this is a decentralized registry.
The association of the username with an identifier is carried out through a transaction on the blockchain where all the details of the user’s account are written.
In this way, the identity of the users has the seal of trust and security of the blockchain.
This allows each person to have a unique user name on the network, to write messages under that user name and to read messages from other people with the confidence that their names are valid.
What happens in conventional social networks such as Twitter or Instagram, is that the company can censor users or limit the scope of their posts.
This does not happen in a farcaster thanks to decentralized registration.
On the other hand, decentralization is not complete because that would mean that users would have to face too many costs, as in the case of each user using their own server.
In order for the network to be scalable and for users not to have to bear such costs, Farcaster advocates that each person should choose the host provider of his or her choice.
And to mitigate the risk of host providers acting in a monopolistic manner and centralizing the network, they make switching hosts very simple.
How they use the blockchain
Farcaster uses the blockchain to perform user registration and store their data and passwords. Everything that has to do with people’s identity.
All other functions such as sending a message, creating a post or following a user, are carried out outside the blockchain.
They only use the blockchain for those operations where security is critical.
0 comentarios